Cyberwarfare
Cyberwarfare can be used to describe various aspects of defending and attacking information and computer networks in cyberspace, as well as denying an adversary’s ability to do the same. Some major problems encountered with cyber attacks, in particular, are the difficulty in determining the origin and nature of the attack and in assessing the damage incurred.
A number of nations are incorporating cyberwarfare as a new part of their military doctrine. Some that have discussed the subject more openly include the United Kingdom, France, Germany, Russia, and China. Many of these are developing views toward the use of cyberwarfare that differ from those of the United States, and in some cases might represent national security threats.
Cyberterrorism is also an issue of growing national interest. Many believe terrorists plan to disrupt the Internet or critical infrastructures such as transportation, communications, or banking and finance. It does seem clear that terrorists use the Internet to conduct the business of terrorism, but on closer inspection, however, it is not clear how or whether terrorists could use violence through the Internet to achieve political objectives.
Although the U.S. government is striving to consolidate responsibility for and focus more attention on cyberwarfare issues, it is not clear how successful those efforts will be. Congress may choose to examine critically the policies, organization, and legal framework that guides executive ranch decisionmaking on issues of cyberwarfare.
Friday, March 26, 2010
CYBERSECURITY LEGISLATION
Mar 26, 2010 (Congressional Documents and Publications/ContentWorks via COMTEX) -- WASHINGTON, D.C. - Senator Jay Rockefeller, Chairman of the U.S. Senate Committee on Commerce, Science, and Transportation, released a draft of bipartisan cybersecurity legislation to address our nation's vulnerability to computer and Internet crime, espionage and attacks. This week, the Commerce Committee favorably reported out Senator Rockefeller's Cybersecurity Act.
"The purpose of this bill is to make absolutely sure that our country is ready in the event of a major cyber attack," said Rockefeller. "Cyber attacks are a 21st century security threat and they call for a rigorous 21st century response. We need a much more well-coordinated and collaborative effort between private sector companies, our citizens and government. We all must work together as a well-practiced team with a winning game plan in order to protect our nation, our networks and our way of life from the growing cyber threat." Senator Rockefeller's legislation would protect the security of the computer networks West Virginians and Americans rely on--not only the computer networks that connect people at home and at work, but also the computer networks that run the state's and nation's banks, schools, power grids, ports and dams, air traffic control system, and so many other critical aspects of American life and the American economy.
The legislation is the culmination of a year's work of consultation and input from cybersecurity experts in the private sector, government and civil liberties community. The bill was marked-up by the Senate Commerce Committee on March 24, 2010.
BACKGROUND The bill provides a framework for engagement and collaboration between the private sector and government on cybersecurity, while protectingcivil liberties, proprietary rights, and confidential and classified information. The bill will: * Create a National Cybersecurity Advisor, modeled on the U.S. Trade Representative, to coordinate the government's cybersecurity efforts and collaborate with the private sector.
* Initiate a new public awareness campaign to make basic cybersecurity principles and civil liberties protections familiar to citizens.
* Support major new cybersecurity R & D and the recruiting of students to study cybersecurity and apply their skills in public service.
* Create a dynamic cycle of market-driven innovation in professional training and cybersecurity products and services.
* Call on the private sector and government to share threat and vulnerability information, including access to classified threat information for cleared private sector executives - along with the responsibility for acting on it.
* Require the President and private sector jointly to develop and rehearse detailed cyber emergency response plans.
Senator Rockefeller's legislation does not give any new or broader authority to the President. It does makes sure we plan for and practice our response to an attack, so that if the President ever had to declare an emergency because of a cyber attack, both the government and private sector would be ready to immediately act to protect our country and our people.
China to blame for repeated cyberattacks
 The computerized critical infrastructure of the US is "severely threatened" by cyberattacks now occurring on an "unprecedented scale with extraordinary sophistication."
The computerized critical infrastructure of the US is "severely threatened" by cyberattacks now occurring on an "unprecedented scale with extraordinary sophistication."
Director of National Intelligence Dennis Blair testifies on Capitol Hill in Washington, Wednesday, before the House Intelligence Committee hearing on the annual threats assessment of the US intelligence community.
Manuel Balce Ceneta / AP
That's the headline Dennis Blair, director of national intelligence, offered the Senate Select Committee on Intelligence Tuesday. But it was the largely unreported details he unpacked that could provide the wake-up call for government and private industry, whose computer networks he says are now under persistent and subtle assault.
In his remarks, Mr. Blair concluded that:
• Sensitive information is “stolen daily from both government and private sector networks.”
• Investigations are finding "persistent, unauthorized, and at times unattributable presences on exploited networks, the hallmark of an unknown adversary...."
• The US cannot be certain its cyberspace infrastructure will be available and reliable in a crisis.
• The US and the world face greater vulnerability to disruption as a result of the trend toward convergence of voice, facsimile, video, computers, and controls that operate critical infrastructure on a single network: the internet. These include banking, power, and water supplies
• Cyberthreats are increasingly subtle and sophisticated. Last year saw the deployment of “self-modifying malware, which evolves to render traditional virus detection technologies less effective.”
Such attacks are already happening, confirmed Daniel Geer, chief information security officer for In-Q-Tel, a nonprofit venture capital firm funded by the Central Intelligence Agency, at a security conference for the oil and gas industry in Houston in November. Other cybersecurity experts cite a growing threat from so-called "polymorphic" spyware that can change its digital signature to millions of different combination to evade identification by anti-virus software.
In this new scenario, a single piece of malware often has multiple characteristics. Its digital signatures can morph to evade detection. At the same time, it can spin off decoys intended to be caught to make it appear as if an attack has been thwarted.
 The recent sophisticated attacks on Google should be a "wake-up call,” Blair said. His remarks echoed recent reports that show the problem is not only coming from clever hackers, advanced viruses, or organized cybercrime gangs – but from “nation states,” too.
The recent sophisticated attacks on Google should be a "wake-up call,” Blair said. His remarks echoed recent reports that show the problem is not only coming from clever hackers, advanced viruses, or organized cybercrime gangs – but from “nation states,” too.
"Many [of the most sophisticated attackers] have the capabilities to target elements of the US information infrastructure for intelligence collection, intellectual property theft, or disruption," Blair said.
Countries see repeated cyberattacks
More than half of the 600 IT managers operating critical infrastructure in 14 countries reported being recently hit by "high-level" adversaries such as organized crime, terrorists or nation states, according to a new global survey of information technology executives by the Center for Strategic and International Studies in Washington late last month.
A majority of the group hit, 59 percent, said they thought their computer networks and controls systems were under "repeated cyberattack, often from high-level adversaries like foreign nation-states."
Blair's comments might be news to the Senate, but cybersecurity experts face these threats daily. The "persistent" threat he referred to, for instance, is known widely as the "Advanced Persistent Threat" or APT within the security community. It's also shorthand for state-sponsored "foreign intelligence" operations and sometimes just "China."
"These are not ‘slash-and-grab jobs’,” says Rob Lee, a director at Mandiant, a leading cyber security firm. "The goal of the intruder is to occupy the network. These are professionals, not people doing this at night. This is someone's full-time job from the initial breach to lateral movement across the network, the actual occupation, then the ex-filtration of data - there are clear lines of responsibility between different actors going on."
Is China to blame?
According to Mr. Lee and other experts, the common thread in the APT is connected to China. Among 40-45 very sophisticated attacks in the past year, about two-thirds were “China related,” he said.
Shawn Carpenter, principal forensics analyst at NetWitness Corporation, concurs. He says that in a number of cases he has traced malware code back to Chinese hacker sites and to Chinese character sets in software compilers used to create the code. "You can put together some pretty compelling links that trace their way back to China," he says.
Representatives of the Chinese Embassy regularly rebut such criticisms, as they did with a Monitor report last month on cyber attacks targeting the US oil and gas industries.
Washington: Internet domain company GoDaddy.com said it planned to stop registering domain names in China, joining Google Inc in protesting cyber attacks and censorship in that country.
"We believe that many of the current abuses of the Internet originating in China are due to a lack of enforcement against criminal activities by the Chinese government," said Go Daddy Group Inc general counsel, Christine Jones.
She said GoDaddy had repelled dozens of extremely serious attacks that appear to have originated in China in the first three months of 2010.
Jones said GoDaddy, based in Scottsdale, Arizona, would continue to manage .cn domain names of existing customers.
"Our experience has been that China is focused on using the Internet to monitor and control the legitimate activities of its citizens, rather than penalizing those who commit Internet-related crimes," Jones said.
Google said in January that it had sustained a hacking attack that it said originated in China. This week Google shut its Chinese portal over censorship and said it planned to phase out deals to provide filtered search services to other online or mobile firms in China.
Google said visitors to its China search engine, google.cn, were being redirected to Hong Kong-based google.com.hk.
"I compliment Google and I compliment GoDaddy," said Democratic Senator Byron Dorgan, chairman of the Congressional-Executive Commission on China, which focuses on human rights in China.
Republican Representative Chris Smith said GoDaddy's action was "a powerful sign that American IT companies want to do the right thing in repressive countries."
Google told the commission it was seeing intermittent censorship of some Internet queries from mainland China that had been rerouted to Hong Kong.
"We are well aware that the Chinese government can, at any time, block access to our services," said Google's director of public policy, Alan Davidson.
"Indeed we have already seen intermittent censorship of certain search queries on both google.com.hk and google.com."
Internet censorship has drawn increased attention from U.S. lawmakers since Google's spat with China began and a policy initiative by US Secretary of State Hillary Clinton to promote global Internet freedom.
"This is a foreign policy priority of the United States," said Democratic Senator Ted Kaufman, co-chair of the Senate's newly formed Global Internet Freedom Caucus.
Card Hackers Albert Gonzalez
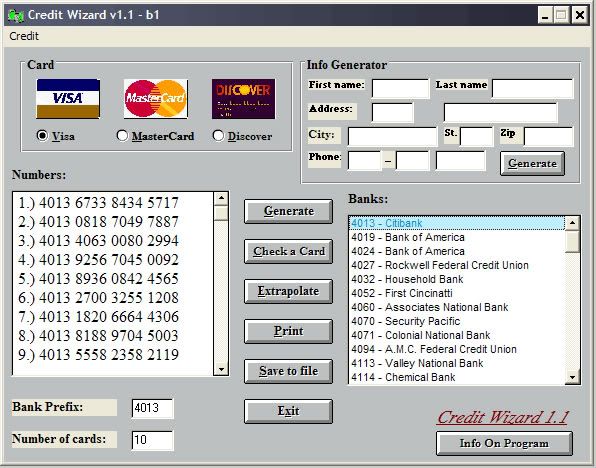
A federal judge sentenced the hacker behind the largest compromise of credit and debit card data in U.S. history to a 20-year sentence this week. While the exploits used to swipe data from over 130 million accounts went beyond cracking passwords, there are some basic precautions businesses should take to protect data from similar breaches and minimize the impact if a breach does occur.
Alberto Gonzales, the attacker behind the notorious data breaches at TJ Maxx, and Heartland Systems--among others--caused nearly $200 million in damages for the companies, banks, and insurers impacted by his attacks. That figure doesn't include the money, time, and mental anguish of the individual customers affected by the data breach.
Kevin Haley, Director Symantec Security Response, expressed via e-mail "Organizations and consumer alike can take precautions to lower their security risk. A first step can be effective passwords."
"People choose passwords based on different factors: how easy they are to remember, how strong or complex they are, the sentimental value they have, etc. Symantec developed a survey to see how users are doing today creating and updating their passwords," added Haley.
The Symantec survey yields some interesting results. Here are some of the key findings:
• 44 percent have more than 20 accounts that require passwords
• 45 percent have just a few passwords that are alternated for all accounts
• 10 percent used their pets name when creating a password (a big no-no)
• 63 percent do not change their passwords very often
Sadly, these results are not all that shocking. It is just the most recent in a long line of surveys illustrating why the password is the weakest link in the security chain in most cases. Businesses that implement cutting edge security tools and lock data down tightly, and then "protect" it all with an administrator account with the password "12345" have essentially not protected anything.
Last year Imperva conducted an exhaustive analysis of the 30 million passwords exposed in the Rockyou breach, and found the following:
• About 30 percent of users chose passwords whose length is equal or below six characters.
• Moreover, almost 60 percent of users chose their passwords from a limited set of alpha-numeric characters.
• Nearly 50 percent of users used names, slang words, dictionary words or trivial passwords (consecutive digits, adjacent keyboard keys, and so on).
The bottom line is that passwords are the primary security control standing between your sensitive and confidential data and a breach or compromise of that data. Complex passwords are difficult to remember, and constantly changing passwords makes committing them to memory even harder--but not using complex passwords, and not changing them periodically greatly increases the risk of a breach.
Passwords are only part of the equation, though. Businesses must also follow other security best practices to prevent unauthorized access and protect data from breaches--especially confidential and sensitive data like account numbers, Social Security numbers, credit card numbers, and other information. For most businesses, protecting these types of data is governed by one or more compliance mandates requiring at least a minimum level of security measures be in place.
Businesses should also have logging and monitoring tools in place. Hopefully the security controls in place will be sufficient to prevent any breach or compromise, but in the event that such an attack occurs, the logging and monitoring tools will hopefully alert IT staff that something suspicious is going on. Logging also provides forensic evidence to help identify when and how an attack occurred, and which servers or data may have been impacted.

Albert Gonzalez, the mastermind behind one of the largest cyber thefts in US history.
Businesses won't have to worry about Alberto Gonzalez for another twenty years, but Gonzalez is a dime a dozen and there is no shortage of hackers seeking out businesses with weak security measures and sensitive data to breach.
Make sure your business isn't the next one making headlines for a data breach by taking basic security precautions and ensuring that the password--the key to the front door--is not easily guessed or cracked.
Tony Bradley is co-author of Unified Communications for Dummies . He tweets as @Tony_BradleyPCW . You can follow him on his Facebook page , or contact him by email at tony_bradley@pcworld.comCard hacker Albert Gonzalez gets 20 years, but cyber crime rising
Albert Gonzalez cost companies and insurers almost $200 million, federal prosecutors say, earning him the longest sentence ever leveled for cyber crime.
Mr. Gonzalez was sentenced in Boston on Thursday for breaking into the computer systems of major retailers in Massachusetts. A separate sentencing Friday will address similar hacking cases in New Jersey and New York involving companies such as 7-Eleven Inc., New England grocery store chain Hannaford, and payment card processor Heartland Payment Systems.
Gonzalez pleaded guilty to all charges. His escapades cost companies, banks, and insurers almost $200 million, federal prosecutors say. His sentence is the harshest ever leveled for computer crime in an American court, said Mark Rasch, former head of the computer crimes unit at the US Department of Justice.
Authorities say Gonzalez's activities suggest a growing sophistication among homegrown hackers who use software to harvest credit-card data and other personal information through vulnerable Internet signals and hacked ATMs. Data are often sold to overseas operators or used to benefit the hackers themselves.
According to a report published this month by the Internet Crime Complaint Center, a joint operation between the FBI and the National White Collar Crime Center, online crime complaints reached 336,655 in 2009, up 22.3 percent from the previous year. Total loss linked to online fraud was $559.7 million, a 111 percent rise.
The report listed nondelivery or nonpayment of goods as the top cyber crime reported to law enforcement in 2009, at 19.9 percent. Rounding out the top five were identity theft (14.1 percent), credit-card fraud (10.4 percent), auction fraud (10.3 percent) and computer fraud (7.9 percent).
Gonzalez fits the profile of most cyber criminals: He is male and lived in Florida, the state with the second-highest number of known perpetrators. California is first.
Hackers typically do not operate alone. In the Gonzalez case, two foreign codefendants helped him retrieve and transfer the data overseas.
However, a Chicago case involving cleaning service workers shows how cyber crime is not just limited to computer geeks – or even men. On Thursday, Cook County Sheriff Tom Dart announced the arrest of seven people – all women – who stole data to purchase more than $300,000 in jewelry, electronics, and other goods.
The data were stolen from as many as 250 patient files from the offices of the Northwestern Medical Faculty Foundation by workers of a nighttime cleaning service. Mr. Dart said the data were used to open new credit accounts at major retailers or to add names to existing accounts. Warrants were issued for two suspects who remain at large.
Riskiest cities for cyber crime
This week computer software maker Symantec ranked the top ten “riskiest online cities” for cyber crimes this month, based on a combination of online spending and availability, the number of infected computers and Internet vulnerability rates. They are:
- Seattle
- Boston
- Washington, DC
- San Francisco
- Raleigh
- Atlanta
- Minneapolis
- Denver
- Austin
- Portland
I'm a nice hacker peeping at the accounts of President Barack Obama
By ANGELA DOLAND (AP) – 23 hours ago
PARIS — He's unemployed and isn't much of a computer expert. The Frenchman accused of infiltrating Twitter and peeping at the accounts of President Barack Obama and singers Britney Spears and Lily Allen says he wanted to reveal just how vulnerable online data systems are to break-ins — and he says he didn't mean any harm.
"I'm a nice hacker," suspect Francois Cousteix told France 3 television Thursday, a day after he was released from police questioning, adding that his goal was to warn Internet users about data security.
"Hacker Croll," as he was known online, is accused of breaking into Twitter administrators' accounts and copying confidential data — as well as peeping at Obama's and the singers' accounts, though he didn't have access to sensitive information about them, a French prosecutor said.
FBI agents sat in on the sessions while French police questioned the young man for two days, said Jean-Yves Coquillat, prosecutor in Clermont-Ferrand, where the suspect will be tried in June for hacking.
If convicted on the charge of breaking into a data system, he risks up to two years in prison and a euro30,000 ($40,068) fine. The suspect lives near Clermont-Ferrand in central France.
"He says it's the challenge, the game, that made him do it," Coquillat said. Officials say preliminary investigations suggest Hacker Croll did not tweet in other peoples' names or try to make money out of his information.
"He had access to elements that were so confidential that he could very well have profited from them" through blackmail, for example, said Adeline Champagnat of the French police office on information technology crimes.
She compared the hacker's actions to "a burglar breaking into the headquarters of a big company, able to look at the files of the all employees and clients, with their passwords and confidential information."
"In a way, he succeeded in taking control of Twitter," Champagnat said.
Twitter, based in San Francisco, declined to comment on the case Thursday.
At one point, Champagnat said, the hacker attempted to find a password for Obama's account but didn't follow through with it. With administrator access, "he didn't even need" Obama's password, she said — but hacking into the president's account wasn't his goal.
Cousteix, who was identified as being 23 or 24, said he just wanted to prove a point about Internet security.
"It's a message I wanted to get out to Internet users, to show them that no system is invulnerable," he told France 3 television.
Hacker Croll confessed to the hacking under questioning, and analysis of his computer backs up his statements, police and the prosecutor said.
The suspect, who lives with his parents and has no college degree, didn't have any special computer training, the prosecutor said.
His technique was to get administrators' e-mail passwords' reset by correctly answering their security questions using information about his prey that he gathered from blogs and other public sites, officials said.
Twitter said in July that it was the victim of a security breach. Co-founder Biz Stone wrote at the time that the personal e-mail of an unnamed Twitter administrative employee was hacked, and through that the attacker got access to the employee's Google Apps account.
The French prosecutor said the suspect infiltrated the accounts of "several" Twitter administrative employees. He was able to access information such as contracts with partners and resumes from job applicants, Coquillat said.
Hacker Croll e-mailed some of the documents to TechCrunch, a widely read technology blog, and it subsequently published some of them, including financial projections. The material was also published on several French sites.
Some of the material was more embarrassing than damaging, like floor plans for new office space and a pitch for a Twitter TV show.
Using the administrator logins, Hacker Croll looked at Twitter details of Obama, Allen, Spears and other well-known personalities and was able to see information such as IP addresses, when they were last connected and when they signed up, French officials said.
Twitter's equivalent of an elusive masked bandit was caught in France this week, according to an Agence France-Presse story citing police sources, after the FBI began working with authorities there. A 25-year-old who goes by the name "Hacker Croll," believed to be responsible for two high-profile Twitter hacking incidents in which both celebrity accounts and internal servers were breached, was reportedly in police custody in the French city of Clermont-Ferrand before being released later on Wednesday.
The hacker was allegedly behind an attack about a year ago in which the Twitter accounts of celebrities ranging from Britney Spears to President Obama were breached; he gained access to a Twitter administrator's password by hacking that administrator's Yahoo Mail account first. (Another, similar incident involving celebrity Twitter accounts had taken place several months prior, also after a sabotage on a weak password; an 18-year-old hacker named "GMZ" claimed responsibility.)
It's also likely that the hacker arrested in France was responsible for an internal Twitter security breach that gave him access to hundreds of sensitive company documents--which he then turned over to industry blog TechCrunch. The TechCrunch incident wasn't mentioned in the AFP story, but since the name "Hacker Croll" was associated with that one, too, it's likely that the same person was responsible.
The hacker, whom AFP reports is unemployed and lives with his parents, appears to have told police what he did to sabotage Twitter's servers and was then released with a court date set for June 24. He was already on authorities' radar for some minor online scam activity, and allegedly has also targeted Facebook and Gmail--though has never attempted to profit financially from his hijinks
Obama's Alleged Twitter Hacker Guessed Passwords
By Jennifer LeClaire
March 25, 2010 1:30PM
Bookmark and Share
A 24-year-old Frenchman who allegedly hacked Twitter accounts of President Obama and other celebrities has been arrested. French police said Francois Cousteix acted on a bet, and he told a TV station, "I'm a nice hacker." Cousteix may also be involved in other Facebook and Twitter hacks, and he could face years in prison instead of a security job.
Related Topics
Hacker
Obama
Security
Latest News
New Measures Target Port Pollution
Former Priest Wins Templeton Prize
A Third of Breast Cancer Is Avoidable
New Dinosaur Species Discovered
GM Goes Green with EN-V Concept Car
On Thursday, French police arrested a man who allegedly hacked into celebrity Twitter accounts in the United States. Among his victims was President Barack Obama.
French authorities described the hacker as a 24-year-old Frenchman. Rather than revealing his true identity, police are publicly calling him "Hacker Croll," a pseudonym the hacker used during his criminal activities. However, the Associated Press has identified him as Francois Cousteix.
"He was a young man spending time on the Internet," French prosecutor Jean-Yves Coquillat told London's Telegraph newspaper. "He acted as a result of a bet, out of the arrogance of the hacker. He is the type who likes to claim responsibility for what he has done."
Easy as 1, 2, 3?
Cousteix allegedly accessed Obama's Twitter page, as well as the Twitter pages of famous people like Britney Spears and Lily Allen, by guessing passwords, according to French police.
Whether Cousteix obtained any sensitive information from the president's micro-blog was not disclosed. However, news reports put Cousteix on the scene of the crime of dozens of Facebook and Twitter account hacks. Cousteix could spend up to two years in prison on each count of hacking if convicted.
"For a long time, when people got caught for doing this stuff, they got some kind of lucrative security Relevant Products/Services job," said Rob Enderle, principal analyst at the Enderle Group. "Nowadays companies realize that providing incentives to people who are hacking this stuff wasn't a wise thing to do."
Although French authorities took the lead on the investigation, they reportedly relied on the Federal Bureau of Investigation to monitor Cousteix's online activities. The FBI also reportedly took part in the arrest of the hacker.
No System is Invulnerable
Cousteix has admitted to hacking. "I'm a nice hacker ... It's a message I wanted to get out to Internet users, to show them that no system Relevant Products/Services is invulnerable," Cousteix told France 3 television on Thursday. He had been released from police questioning on Wednesday.
Cousteix also leaked some internal Twitter documents to web sites, including TechCrunch in July. At that time, Twitter cofounder Biz Stone said he thought the hacker was able to access an employee's Google Apps account, which contained Docs, Calendars and other Google apps Twitter relies on for sharing notes, spreadsheets, ideas, financial details, and more within the company.
Stone also stressed that the stolen documents downloaded and offered to various blogs and publications were not Twitter user accounts, nor were any user accounts compromised, except a screenshot of one person's account. In that case, Twitter contacted the user and recommended a password change.
"We'll wee what happens, but I have a feeling that hacking into the U.S. president's Twitter account is not something that's going to result in a pat on the head and a lucrative job," Enderle said. "But the hacker is right. It does show that these social networks are fairly vulnerable. Then again, they are also pretty public. The value of stealing somebody's Twitter account is relatively low unless you use that to run a scam."
Thursday, March 18, 2010
Federal Communications Commission wider cybersecurity role
Plan calls for securing communications networks against cyberthreats

By Jaikumar Vijayan
Click on the link for the 360-page broadband plan.
The National Broadband Plan released by the Federal Communications Commission this week contains several recommendations that are designed to boost the preparedness of communications networks to deal with cyberthreats.
The plan gives the FCC a greatly enhanced role in developing and promoting cybersecurity measures and calls for closer cooperation between the FCC and the U.S. Department of Homeland Security on security matters.
The 360-page broadband plan is a blueprint for modernizing the country's aging communications networks and for delivering broadband services to a majority of U.S. homes over the next decade. It contains six long-term policy goals and other recommendations for ensuring the availability of affordable 100Mbit/sec. service to 100 million U.S. homes, and 1Gbit/sec. service to institutions such as hospitals and schools, by 2020.
While a vast majority of the recommendations deal with building out the communications infrastructure, several touch on cybersecurity and communications networks' ability to survive a cyberattack.
One key recommendation calls on the FCC to develop a cybersecurity "road map" in collaboration with the executive branch. The recommendation gives the FCC 180 days to identify the top five cyberthreats facing the communications infrastructure and to come up with a two-year plan for addressing those threats.
The plan also requires the FCC to enhance its network outage reporting requirements for broadband service providers. The "timely and disciplined" reporting of network outages will help the FCC better understand the causes of cyberattacks and develop more effective responses to them.
One recommendation calls for the FCC and the DHS to collaborate on a cybersecurity information reporting system (CRIS). Currently, the FCC, others government agencies and Internet service providers lack the "situational awareness" needed to identify and respond in a coordinated fashion to large-scale cyberattacks, the plan noted. The FCC and the DHS need to develop an IP network CRIS that would quickly disseminate information to providers about unfolding cyberattacks. The CRIS should be a real-time, voluntary threat-monitoring system, with the FCC acting as a "trusted facilitator" to ensure reciprocal information-sharing among participants in the system, the plan states.
The FCC and the National Communications System will also work on creating priority network access and routing capabilities for broadband users in law enforcement and public safety roles. The goal is to ensure that critical, "time-sensitive, safety-of-life information" does not get lost or delayed because of network congestion issues.
The plan also directs the FCC to explore network resilience and preparedness to deal with simultaneous failure or damage to major network components and facilities. As part of the effort, the agency will examine the ability of commercial networks to withstand major traffic overloads that might result from a bioterrorism attack or a pandemic
The recommendations reflect concern over the perceived susceptibility of U.S. critical infrastructure targets to major cyberattacks. The broadband document refers specifically to the recent attacks on Google and several oil companies as examples of the sort of threats facing the U.S. government and industry. Private sector networks in the U.S. "have been a major target for attacks," the document noted.
"Despite the significant resources that the private sector devotes to cybersecurity, there have been a number of successful attacks on its networks," the document stated, calling for sufficient defenses to protect networks against them.
The Cybersecurity Act, S. 773
Current version of Senate legislation eliminates provision that permitted the president to shut down the Internet in the event of a major cyber attack.
Elizabeth Montalbano

The Senate Wednesday re-introduced a cybersecurity bill it considered last year, minus a provision that would have allowed the president to shut down the Internet in the event of a major cyber attack.
The Cybersecurity Act, S. 773, co-sponsored by Senators Jay Rockefeller (D-W.Va.) and Olympia Snowe (R-Maine), is aimed at protecting critical U.S. network infrastructure against cybersecurity threats by fostering collaboration between the federal government and the private sectors that maintain that infrastructure.
The legislation was originally introduced last April in a two-bill package that together called for the creation of a national cybersecurity adviser, as well as aimed to revise cybersecurity processes and oversight in government, facilitate public-private partnerships on keeping computer systems safe, fund cybersecurity research, and encourage the hiring of more cybersecurity specialists.Companion legislation that would create the national cybersecurity adviser position -- the National Cybersecurity Advisor Act, S.778 -- is still pending before the Senate Committee on Homeland Security and Government Affairs.
The new Cybersecurity Act more or less maintains the goals of the original bill, but also has some key differences.
One big one is that it no longer gives the president unilateral power to disconnect networks from the Internet in the event of a major cyber attack.
As written now, the bill requires the president to work with organizations that own critical network infrastructure to come up with cybersecurity emergency response plans rather than take action on his own.
The bill also includes new provisions. One creates a process for the president and those in the private sector that maintain and own critical infrastructure to come together to decide which IT systems are most crucial to national security and how they should be secured.
Another provision requires the president to provide security clearances to some private-sector officials at those organizations so they have access to classified cyber-threat information they wouldn't otherwise be privy to.
Cybersecurity is a major priority for the Obama Administration, which requested $866 million to protect networks and data in its recently announced fiscal 2011 budget.
Though that figure is slightly less than what was allocated in 2010, officials maintain cybersecurity remains top of mind for the administration, a sentiment reflected in the reintroduction of the Senate bill and other recent government actions.
The House last month passed its own cybersecurity bill, the Cybersecurity Enhancement Act of 2009 (HR 4061), first introduced by Rep. Daniel Lipinski (D-IL) last year.
That bill, though not as broad in scope as the Senate bill, funds research and development for a comprehensive cybersecurity plan that would involve the cooperation of several federal agencies.
The Department of Homeland Security also is taking steps to foster better communication between government intelligence officials and private-sector organizations looking after critical networks.
Through a pilot program the DHS recently launched, CIOs and CSOs from state and local governments as well as private-sector organizations will periodically be allowed to access classified intelligence information regarding cyber threats from state and local fusion centers.
Friday, March 5, 2010
Cyber terrorism AFCOM , RSA Conference 2010
Data centers tackling cyber terrorism
Typical IT shop unprepared, AFCOM says By Jon Brodkin, Network WorldThe data center is receiving more public scrutiny than ever before, with IT managers facing a range of challenges from making systems run more efficiently to protecting computers from cyber terrorism, says AFCOM chief executive Jill Eckhaus
The 30-year-old organization for data center managers is holding its twice-yearly Data Center World show from March 7-11 in Nashville, Tenn., where IT folks will learn about the most pressing issues facing data centers today and share their own experiences.
Gov't builds secret database to fight cyber-terrorismCyber terrorism is one of the topics Eckhaus is looking forward to examining further. AFCOM’s recent survey of more than 400 data center pros found that only one-third have included cyber terrorism in disaster recovery plans, only one-quarter have addressed cyber terrorism in policies and procedures manuals, and only one-fifth provide cyber terrorism employee training. These low numbers were recorded despite the fact that 61% of data center managers said they recognize cyber terrorism as a threat they need to address.
No data center manager is likely to ignore security, but AFCOM officials say they need to recognize that cyber terror poses a more serious threat than a typical hacker.“A hacker might be a student just looking for a challenge,” Eckhaus says. “Cyber terrorists want to destroy the United States. That’s the difference.”
AFCOM will host two sessions on cyber terrorism during the conference. Unfortunately, in a bad economy companies that already have security plans “tend to say what we have is good enough,” Eckhaus says. “They’re really at the very beginning stages.”
Even beyond security, public scrutiny of data centers seems to be increasing, as the 24/7 business world expects computer systems that never fail or slow down. Eckhaus says this is both good and bad for data center managers, because the public is recognizing the important work they do, but also demanding more.
“This is a really unique time, because for the first time in history the data center is in the public eye,” Eckhaus says. “People are starting to understand how vital data centers are. We could not do business as usual without data centers.”
Corporate management is demanding that data centers run more efficiently, both to save money on power costs and to appear environmentally friendly in the public eye, Echuas notes. Going green is important, in part because providing enough power and cooling to data centers is becoming more difficult, she says. But the IT industry is “saturating” data center managers with the green buzzword, she says.
“It’s a buzzword that’s been around for a few years, because the data center sucks up so much energy,” Eckhaus says. “Corporate management is really looking down at the data center now and saying ‘what are you going to do.’”
Even as data centers strive to reduce power consumption, they must deal with the reality that demand for information services is growing. Storage needs are booming, as is global Internet traffic and use of mobile Internet devices, says Brian Lillie, who is CIO of co-location provider Equinix and the keynote speaker at the Data Center World conference.
FBI Director Promises Privacy, Information About Attacks To Breach Victim Organizations
Robert Mueller tells attendees FBI 'cannot act' if businesses don't report cyberattacksMar 05, 2010 | 07:55 AM
By Kelly Jackson HigginsDarkReading
SAN FRANCISCO -- RSA Conference 2010 -- Organizations are typically hesitant to disclose cyberattacks to the FBI, and their disclosure is "the exception, not the rule," FBI director Robert Mueller told attendees here today in a keynote address.
Mueller said the bureau understands organizations' concerns about privacy and image when it comes to deciding whether to report a cyberattack to the authorities, but promised the FBI would provide more information-sharing and protection of victim organizations' privacy.
"We do not want you to feel victimized a second time by an investigation. And we know that putting on raid jackets, courting the media, and shutting down your systems is not the best way to get the job done," he said. "We will minimize the disruption to your business. We will safeguard your privacy and your data. Where necessary, we will seek protective orders to preserve trade secrets and business confidentiality. And we will share with you what we can, as quickly as we can, about the means and methods of attack."
Mueller cited a recent partnership between the financial industry and the FBI to put together an intelligence report on threats in banking transactions. "We shared that report with more than 4,000 partners. Together we worked to limit the breadth and scope of this potential threat, and we closed the door to countless hackers," Mueller said. He did not provide any details on the threats or the report.
Meanwhile, the threat of cyberterrorism is "real and rapidly expanding," Mueller said. "To date, terrorists have not used the Internet to launch a full-scale cyberattack. But they have executed numerous denial-of-service attacks. And they have defaced numerous Websites, including Congress' Website following President Obama's State of the Union speech," he said, referring to the so-called Iranian Cyber Army hacking group.
"We in the FBI, with our partners in the intelligence community, believe the cyber terrorism threat is real, and it is rapidly expanding. Terrorists have shown a clear interest in pursuing hacking skills. And they will either train their own recruits or hire outsiders, with an eye toward combining physical attacks with cyberattacks."
Targeted attacks for intelligence and espionage are also a major threat, according to Mueller. He noted that intelligence-gathering efforts by hackers to grab "seemingly innocuous" data about a company can provide them a foot in the door into the company's network.
These targeted attacks have resulted in the loss and corruption of victims' data. "We are concerned with the integrity of your source code. If hackers made subtle, undetected changes to your code, they would have a permanent window into everything you do," he said.
The FBI and other law enforcement officials are currently reverse-engineering botnets with plans to knock them offline: Most recently, the collaborative effort resulted in the takedown of the Mariposa botnet.
Mueller said the FBI has special agents "embedded" with law enforcement in Romania, Estonia, and other countries to help coordinate cybercrime investigations. "Together we are making progress. Last October we worked with Egyptian authorities to dismantle a computer-intrusion and money-laundering scheme operating in the United States and Egypt," he said.
FBI Wants You For The mobile cyberaction teams
Mueller
to Cybersecurity Experts:
The FBI Wants
You


By Richard Adhikari
TechNewsWorld
The Federal Bureau of Investigation on Thursday joined the Department of Homeland Security in seeking to hire cybersecurity experts from the private sector.
"I want to send out an invitation to those of you in the audience who want to serve the country to join the FBI," FBI Director Robert Mueller said at the RSA Conference 2010 in San Francisco on Thursday.
Mueller also urged the private sector to cooperate with the FBI in fighting cybercrime, as did DHS Secretary Janet Napolitano when she spoke at RSA 2010 on Wednesday.
Taking On More Staff
The FBI has cybersquads in each of its 56 fields nationwide, and more than 1,000 specially trained agents, analysts and digital forensic examiners who run complex undercover operations, share intelligence with partners in law enforcement and intelligence, and provide training to their counterparts around the world, Mueller said.
It also has mobile cyberaction teams -- agents, analysts and experts highly trained in both computer forensics and malicious code -- who travel worldwide to respond to fast-moving cyberthreats.
In addition, it has created and leads the National Cyber Investigative Joint Task Force, which combines 17 law enforcement and intelligence agencies to predict what's on the horizon, to prevent attacks, and to pursue the enterprises responsible for planning them.

The FBI also has small groups of analysts and agents from different agencies who focus on different threats, Mueller said. For example, its botnet fusion focus cell investigates high-priority botnets, reverse engineers those botnets, and searches for their creators.
However, that's not enough; the FBI is seeking to beef up the ranks of its cybersecurity experts.
"We -- both you and I -- serve the American people, and we must do everything we can together to minimize and stop these attacks," Mueller said. Without support from the private sector, law enforcement will find it difficult to fight cybercrime, Mueller said.
"We need your help, so let me emphasize the importance of private sector partnerships," he told his audience.
Mueller pledged that the FBI will minimize disruption to companies that report crimes.
"Historically, there has been a dichotomy between network security and the investigative process," he pointed out. "We in the FBI understand you have practical reasons for being concerned about reporting breaches of security."
The FBI doesn't want enterprises to feel victimized a second time by an investigation, Mueller promised.
"We know that putting on raid jackets, courting the media, and shutting down your operations does not get the job done," he said, echoing what he said in 2005 when he complained about the reluctance of the private sector to report cybercrime. "For every investigation in the news, there are hundreds that never make the headlines. Disclosure is the exception, not the rule."
Private enterprises have been reluctant to report cyberattacks for fear that investigations will hurt their operations, a fact acknowledged by the U.S. Department of Justice and other law enforcement agencies.
"We will share with you what we can as quickly as we can about the means and the methods of the attacks," Mueller said, "but we cannot act if we are not aware of the problem, and maintaining a code of silence will not help you or your clients in the long run."

For example, the FBI managed to crack a crime ring that stole millions of dollars from more than 280 cities worldwide within 24 hours by using fake ATM cards because the company in question reported the crime, Mueller said.
"In 24 hours, the attackers stole hundreds of millions of dollars in more than 280 cities worldwide," Mueller told his audience. "If the company hadn't come forward, we could not have prevented these hackers from hitting their next victim."
The top three hackers behind this attack are now in custody in eastern Europe, Mueller said.
A New World Cybersecurity Order
Fighting cybercrime effectively requires international cooperation among nations and law enforcement, Mueller pointed out. "Today, no one country, no one company, no one agency can stop cybercrime," he explained. "We see borders as obstacles, whereas criminals see them as opportunities."
Cybercriminal gangs cooperate easily across national borders, while law enforcement agencies cannot because of jurisdictional and legal issues and other differences. Some countries also protect well-connected cybercriminals.
The FBI has more than 60 attachés based in nations around the globe who share information and intelligence with their host countries, Mueller pointed out.
Cooperation between the FBI and Spanish authorities helped crack the Mariposa botnet and take down the three men behind it.
"This case, like so many others, emphasizes the need for global cooperation," Mueller said.
The FBI has also cooperated with Egyptian authorities to dismantle an intrusion and money-laundering scheme, and with German and other authorities to dismantle "Dark Market," one of the largest underground markets for stolen cyberinformation.
"Together we must work towards an international standard for dealing with cybercrime," Mueller said. "We're playing the cyberequivalent of cat and mouse, and the mouse seems to be one step ahead most of the time."
